SecureBug CTF Reverse Writeups
- 8 minsRevMeBro
We were provided by an android apk file named RevMeBro.apk that has a simple flag checking algorithm so i fed it into jadx-jd to know about the algorithm
Below attached image is the main entry function
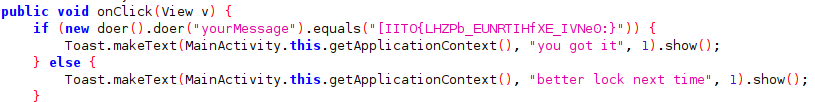
And we can see that the input is is moved to doer and then compared with the string [IITO{LHZPb_EUNRTIHfXE_IVNe0:}
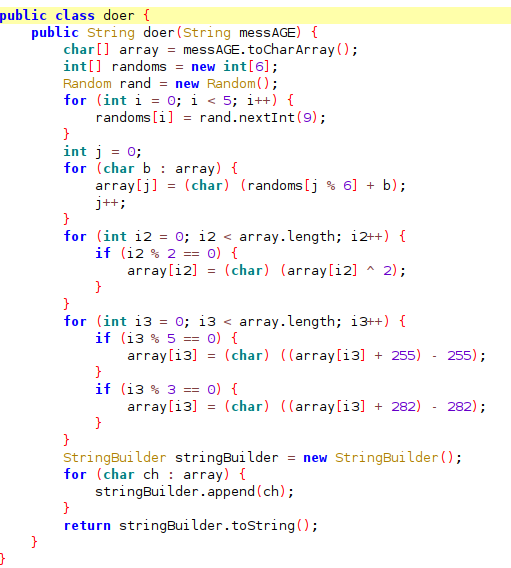
Let’s Build the algo in python3
import random
a = "inputflag"
k = []
for i in range(5):
k.append(random.randint(1,8))
for i in range(len(a)):
a[i] = chr(k[j%6]+ord(a[i]))
if(i%2==0):
a[i] = chr(ord(a[i])^2)
The flag initials are SBCTF and the comparing flag given is 1st 5 chars are [IITO
Let’s build the random array from it
a = list("SBCTF{")
b = list("[IITO{")
k =[]
for i in range(6):
if(i%2==0):
b[i] = chr(ord(b[i])^2)
k.append(ord(b[i])-ord(a[i]))
print(k)
This would give you out
randomarray = [6, 7, 8, 0, ,0]
Now Let’s again reverse the whole flag
randomarray = [6, 7, 8, 0, 7,0]
a = list("[IITO{LHZPb_EUNRTIHfXE_IVNe0:}")
inputflag = []
for i in range(len(a)):
if(i%2==0):
a[i] = chr(ord(a[i]) ^2)
inputflag.append(chr(ord(a[i])-randomarray[i%6]))
print("".join(inputflag))
It will output the flag SBCTF{HAPPY_ANDROID_REVING_01}
BatmanSafe
In this challenge we are being provided with a ELF file name Safe.Run the ELF is a shared object first i thought to try angr but then as it’s not an executable it wasn’t running so i would now it’s time for static reversing :)
Safe.Run: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=1fe7719fa966629756b4d92775e03f124a446fca, for GNU/Linux 3.2.0, not stripped
As we can see it’s not stripped and dynamically linked so a task is reduced Let’s grep for GCC
GCC: (Ubuntu 9.3.0-17ubuntu1~20.04) 9.3.0
and a basic look from strings show
Wrong combination
Bye!
Enter your Name
Enter combination
SBCTF{
And when you run it normally it asks a Name and a Combination which is a kinda serial number
Let’s feed it in IDA
As you can see the image this is my usual IDA setup while reversing with Sync On between disassembly and PSEUDOCODE
PS: :P ignore the naming i usually rename in CTFs like this only for fun
Okay now let’s get back to work
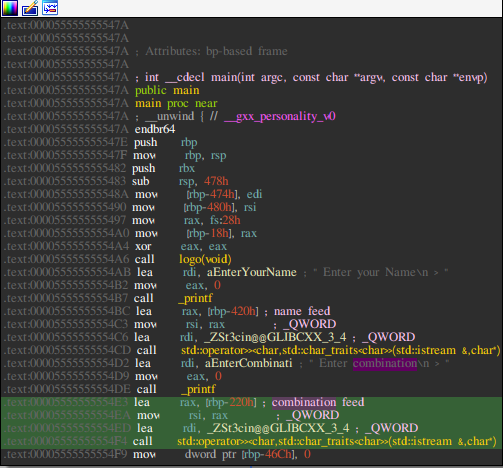
As you can see the combination feed comments at addr 0x5555555554DE and at addr 0x5555555554bc Name variable is saved from the address [rbp-0x420h] and Combination Variable is saved at [rbp-0x220h]
Remember this i will tell you why
Ok now take a look at the pseudocode
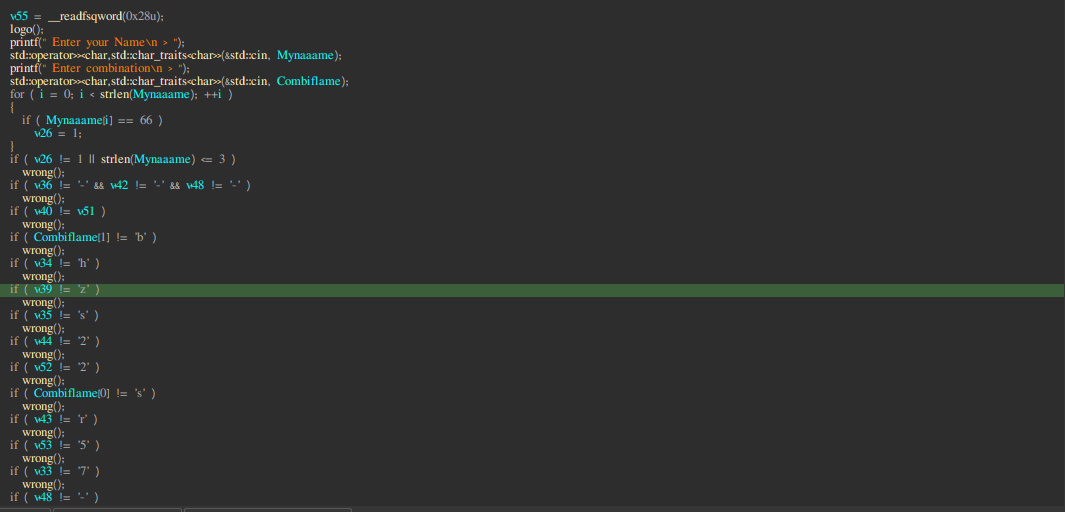
You can findout some basic things from the pseudoCode that:
- Mynaaame should have 1 char as ‘B’ (ascii code 66)
- strlen of Mynaaame should be greater than 3
- CombinationCode’s first char should be
sand 2nd char should beb - if you would scroll down a little you would see Combination’s Code should be greater than 19
Through some of these let’s say we put the name as BatmanSafe and Combination Code as sbabcdefghijklmnoprs and run the program in gdb put a break point at 0x000055555555556C
at the breakpoint run some commands x/b $rbp-0x21b it will output 0x64 hexcode for ‘d’ that is 6th char in our Combination Code and the variable it’s assigned is v36
so 6th character is assigned v36 that means it’s an array; let’s go no on behalf of this you can check some other variables also if you are beginner to confirm and go through gdb just put a breakpoint on every mov that puts [rbp-0x2{}{}] into rax and check that value if it satisfies
While going through pseudoCode you will the last variable in comparison is v53 so lets change the the Ivar type of Combiflame from char Combiflame[2] to char Combiflame[25] for 25 characters
After changing the Ivar type your psuedoCode will look something like this
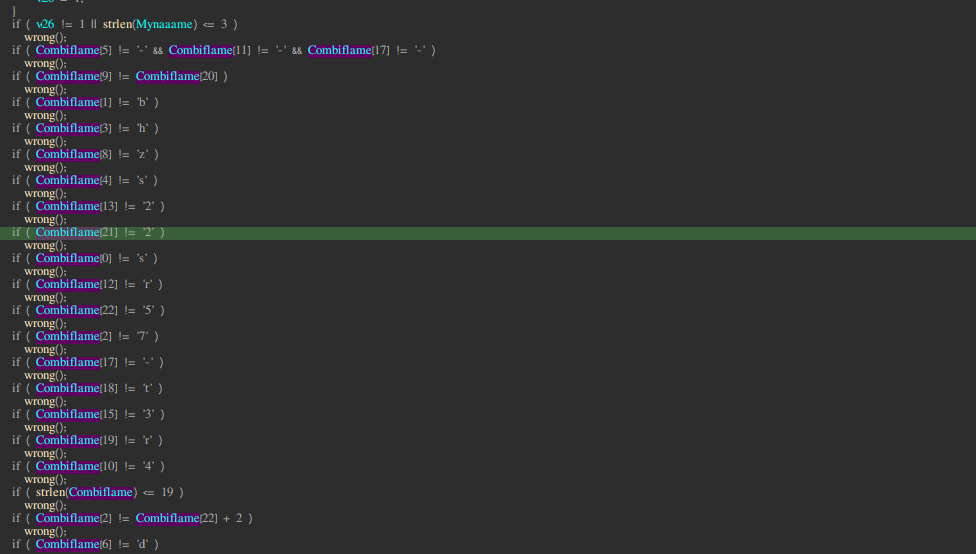
Now at this point :P I just mannually wrote down the combination Code
sb7hs-dhza4-r2d3z-tra25
That gave me the flag SBCTF{The_BUttoN}
Superman
We are given an 32bit exe file, ok as being in Malware Analysis i just fired up DIE(Detect It Easy) to take a look at the sample
Some Points to note:
Microsoft Visual C++(-)[-]
Microsoft Linker(14.28**)[Console32,console]
- checking if packed or not: Not Packed
Looking for strings something interesting:
They drew whole Superman as an ascii nice
Ok let’s fireup the VM (Windows 7 x64bit Disabled ASLR and DEP)

Now let’s fireup ida to take a look
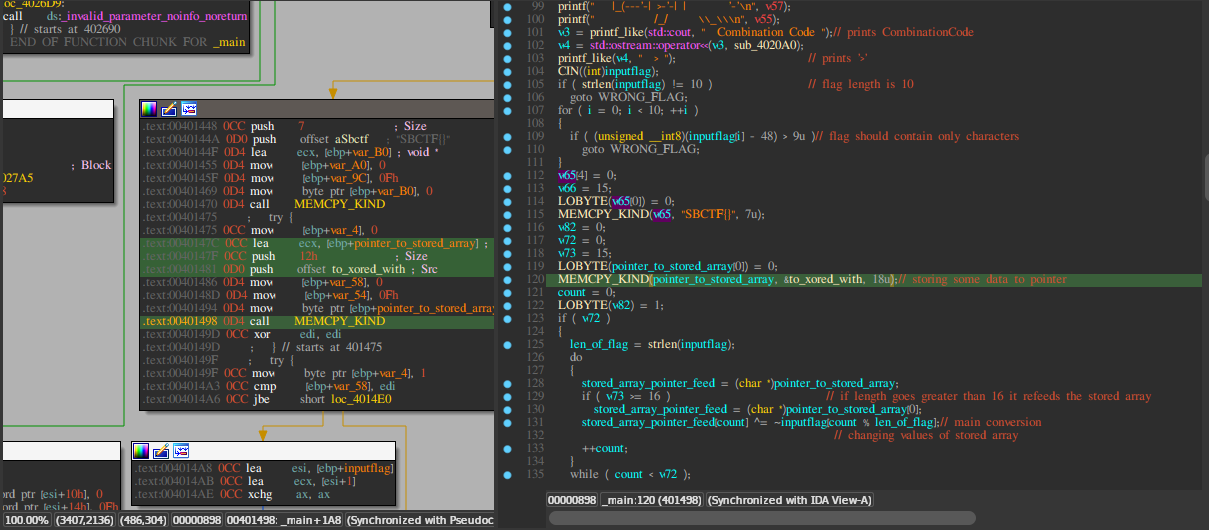
This is how my IDA Looks normally when i am reversing :)
Turn on Demangled Names from Options and Line Prefixes(Graph) from Options->General
Again to note down some points from the pseudoCode as i tried to clean it as possible
Let’s go through its algo
- Takes flag as input
- Checks if flag length is 10
- Characters of flag should be only integers
- Put some stored data into a array through memcpy
- XORs the stored array with the input
- Compares the xored array with the stored checking ifs.
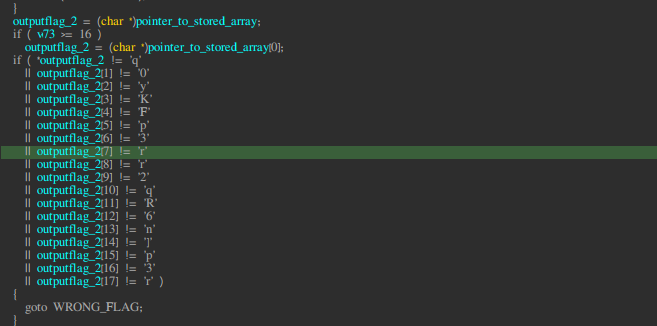
Initially I wasn’t able to properly clean the psuedoCode that’s when i took up to x64 debugger to look for the xoring disassembly
And as i told you that i have disabled ASLR so it simply just put the breakpoint by looking at ida at the same addr.
Let’s break at the XORing point.
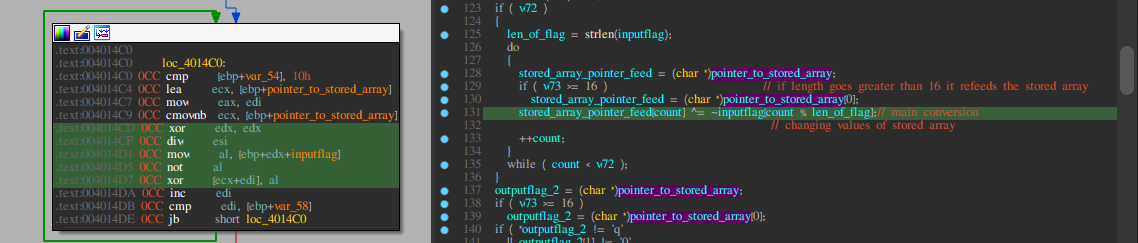
I feed the system code 1234567890.
Let’s break down the mechanism again:
-
At 0x004014D1 mov al,byte ptr ss:[ebp+edx-1C] 1is being fed into al -
At 0x004014D5 not al not of 1is done that is 0xCE -
At 0x004014D7 xor byte ptr ds:[ecx+edi],al NOT of 1is being xored with 1st character of stored array that is 0xbf
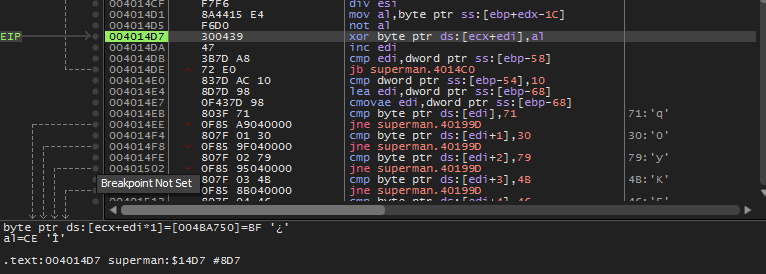
- The counter is increased and again same process is repeated till 18th length
Let’s make the python script to reverse this
storedArray = [0xBF,0xFC,0xB5,0x83,0x81,0xBD,0xFD,0xBF,0xBD,0xFD,0xBF,0x9E,0xFA,0xA6,0x9A,0xBD,0xFD,0xBF]
xoredString = "q0yKFp3rr2qR6n]p3r"
k = []
for i in range(18):
k.append(chr(~(storedArray[i]^ord(xoredString[i]))&255))
print(''.join(k)[:10])
This would give us the code 1337821200
Putting it in the gives us the flag SBCTF{major_exe}